SingleStore Studio Security
On this page
Important
Studio is designed to work with MemSQL 6.
Authentication
SingleStore Studio (or simply "Studio") is a visual SQL client that connects to your SingleStore clusters.
Logging In
To login to a cluster from Studio, you must use the same username and password that you would use when connecting through an application such as the MySQL client, and the host value must either be a wildcard, or the name of the computer that's running Studio.
Logging in Using Kerberos
As of Studio 1.
Once configured, Studio will work as any other application that uses Kerberos authentication inside a browser.
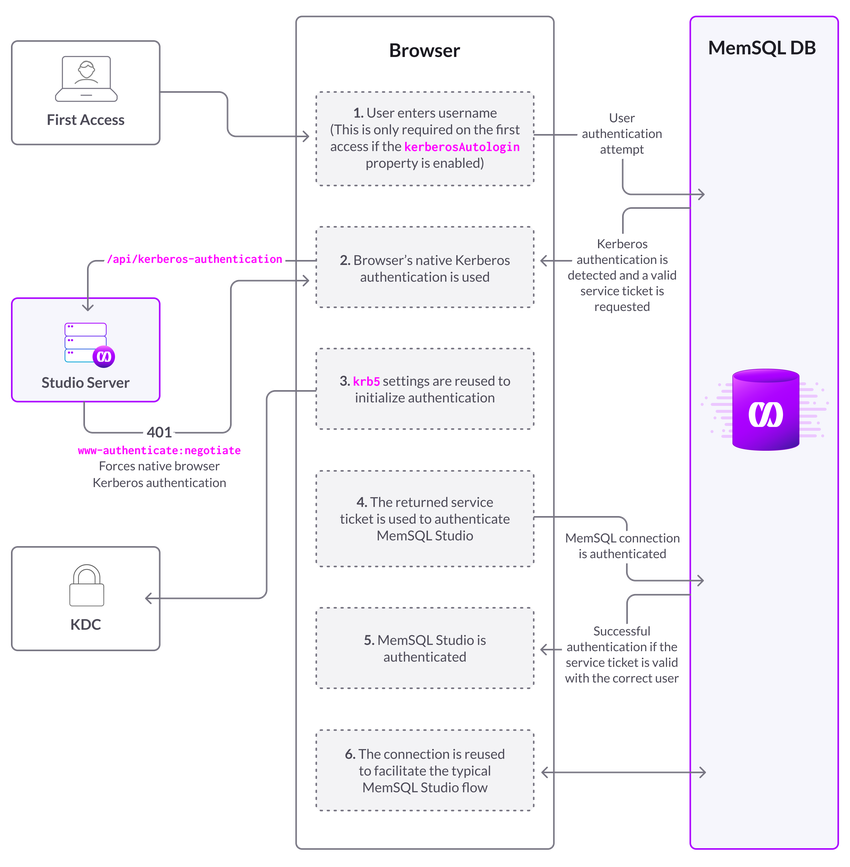
Kerberos Authentication Flow
The Kerberos authentication flow is depicted in the following diagram.
Kerberos authentication flow
Configuring Kerberos Authentication
Prerequisites
-
As Studio authentication relies on SingleStore engine authentication, complete the steps in Kerberos Authentication before configuring Kerberos in Studio.
-
Confirm that your browser has Kerberos configured.
-
(Optional) To allow Studio to automatically log in with the current Kerberos user, set the
kerberosAutologinproperty totruein the Studio state file.You must restart Studio after changing this configuration.
Configuration Example
-
Studio is served under the CNAME
auth-server..example. com -
The Kerberos Realm is
example..com -
Studio is accessed from
auth-server..example. com
This example uses the configuration detailed in the Kerberos SPN generation section of The Chromium Projects’ HTTP authentication.
Use the following steps to configure Studio to allow Kerberos authentication.
-
Register SingleStore Studio as a trusted client in Kerberos
Create a Kerberos Service Principal Name (SPN) of
HTTP/auth-server.for authentication.example. com@EXAMPLE. COM This is the default SPN generated by the browser. This SPN must be added to your KDC as a trusted new client. Your SPN must be created in the domain from which Studio is run. -
Generate the
keytabUsing
ktutil, generate a newkeytabthat includes the SPN. -
Update the SingleStore engine variable
The
gssapi_engine variable is defined with the desired SPN (in this example,principal_ name HTTP/auth-server.).example. com@EXAMPLE. COM To update this variable, run the following command. SET GLOBAL gssapi_principal_name = <your_SPN>;The SPN is also added to the Kerberos
keytabfile and defined ingssapi_.keytab_ path To list the SPNs associated with a keytab, run the following on the command line:klist -ket /path/to/name.keytab
Running Queries
Once logged in, all queries from Studio against a cluster are run with the user’s cluster credentials.
To query the materialized views (MV_SHOW METADATA permission.
Serving the UI with HTTPS
To serve the Studio user interface with HTTPS, edit the Studio configuration file to include the following two options.
HTTPSCertificateFile = "./server.crt"
HTTPSCertificateKeyFile = "./server.key"-
The
HTTPSCertificateFilekey must point to the path of the public certificate that you’d like to use for HTTPS. -
The
HTTPSCertificateKeyFilemust point to the path of the key file.
Where:
These paths can be absolute or relative to the Studio binary, although the absolute path is recommended.
Test the Connection
To confirm that the connection to Studio is secure and the certificate is valid, launch a Chrome or Firefox browser and attempt to connect to Studio using HTTPS.
Configuring TLS Versions and Cipher Suites
As of version 3.
To enforce the use of specific TLS versions and cipher suites by the Studio server, modify the Studio configuration file (singlestoredb-studio.) by including TLSVersions and TLSCipherSuites properties in the following format.
TLSVersions = ["TLSv1.1", "TLSv1.2"]
TLSCipherSuites = ["ECDHE-ECDSA-RC4-SHA", "ECDHE-ECDSA-AES128-SHA", "ECDHE-ECDSA-AES256-SHA", "ECDHE-RSA-RC4-SHA", "ECDHE-RSA-DES-CBC3-SHA", "ECDHE-RSA-AES128-SHA", "ECDHE-RSA-AES256-SHA"]The TLSCipherSuites property takes OpenSSL cipher suite names as values.
Be sure to specify consecutive protocol versions when configuring multiple protocols.TLSVersions = ["TLSv1., TLSv1.TLSVersions = ["TLSv1..
Note
-
TLS versions and cipher suites may only be used with HTTPS.
-
If
TLSVersionsandTLSCipherSuitesproperties are not included or are left empty in the Studio configuration file, all of the supported TLS versions and their cipher suites will be permitted. -
TLS version and cipher suite configurations apply to the Studio server (the "server side").
Supported TLS Cipher Suites
|
Cipher Suite (OpenSSL) |
Cipher Suite (IANA) |
TLS Versions Supported |
|---|---|---|
|
RC4-SHA |
TLS_ |
Up to TLSv1. |
|
DES-CBC3-SHA |
TLS_ |
Up to TLSv1. |
|
AES128-SHA |
TLS_ |
Up to TLSv1. |
|
AES256-SHA |
TLS_ |
Up to TLSv1. |
|
AES128-SHA256 |
TLS_ |
TLSv1. |
|
AES128-GCM-SHA256 |
TLS_ |
TLSv1. |
|
AES256-GCM-SHA384 |
TLS_ |
TLSv1. |
|
ECDHE-ECDSA-RC4-SHA |
TLS_ |
Up to TLSv1. |
|
ECDHE-ECDSA-AES128-SHA |
TLS_ |
Up to TLSv1. |
|
ECDHE-ECDSA-AES256-SHA |
TLS_ |
Up to TLSv1. |
|
ECDHE-RSA-RC4-SHA |
TLS_ |
Up to TLSv1. |
|
ECDHE-RSA-DES-CBC3-SHA |
TLS_ |
Up to TLSv1. |
|
ECDHE-RSA-AES128-SHA |
TLS_ |
Up to TLSv1. |
|
ECDHE-RSA-AES256-SHA |
TLS_ |
Up to TLSv1. |
|
ECDHE-ECDSA-AES128-SHA256 |
TLS_ |
TLSv1. |
|
ECDHE-RSA-AES128-SHA256 |
TLS_ |
TLSv1. |
|
ECDHE-RSA-AES128-GCM-SHA256 |
TLS_ |
TLSv1. |
|
ECDHE-ECDSA-AES128-GCM-SHA256 |
TLS_ |
TLSv1. |
|
ECDHE-RSA-AES256-GCM-SHA384 |
TLS_ |
TLSv1. |
|
ECDHE-ECDSA-AES256-GCM-SHA384 |
TLS_ |
TLSv1. |
|
ECDHE-RSA-CHACHA20-POLY1305-OLD |
TLS_ |
TLSv1. |
|
ECDHE-ECDSA-CHACHA20-POLY1305-OLD |
TLS_ |
TLSv1. |
|
TLS_ |
TLS_ |
TLSv1. |
|
TLS_ |
TLS_ |
TLSv1. |
|
TLS_ |
TLS_ |
TLSv1. |
Note
The TLSCipherSuites property cannot be used when TLSv1.TLSCipherSuites property.
Enabling HTTP/2
As of version 3.EnableHTTP2 property to true in the Studio configuration file.
EnableHTTP2 = trueNote
HTTP/2 may only be used with HTTPS.
Encrypted connections via HTTP/2 over TLS 1.
-
HTTP/2 deployments over TLS 1.
2 should not use any cipher suites listed in the TLS 1. 2 Cipher Suite Black List as it may result in a connection error. -
This black list includes the mandatory cipher suite for TLS 1.
2, which means that TLS 1. 2 deployments could have non-intersecting sets of permitted cipher suites. To avoid potential TLS handshake failures, deployments of HTTP/2 that use TLS 1. 2 must support TLS_[TLS-ECDHE] with the P-256 elliptic curve [FIPS186].ECDHE_ RSA_ WITH_ AES_ 128_ GCM_ SHA256
For more information, see related IETF documentation.
Configuration File
The following is an example configuration file with HTTPS, TLS, and cipher suite settings.
# This is the IP address that SingleStore Studio will bind to.
host = "0.0.0.0"
# This is the port that Studio will bind to.
port = 8080
# This is the absolute path to the state file of Studio.
statePath = "/PATH/TO/studio.hcl"
# This is the absolute path to the log file of Studio.
logPath = "/PATH/TO/studio.log"
# This is the absolute path to the SSL certificate used to serve Studio UI with HTTPS.
HTTPSCertificateFile = "/PATH/TO/server.crt"
# This is the absolute path to the key file of the SSL certificate used to serve Studio UI with HTTPS.
HTTPSCertificateKeyFile = "/PATH/TO/server.key"
# This property specifies the TLS protocol versions that can be used for Studio’s connections with the browser
TLSVersions = ["TLSv1.1", "TLSv1.2"]
#This property specifies the TLS cipher suites that can be used for Studio’s connections with the browser.
TLSCipherSuites = ["ECDHE-ECDSA-RC4-SHA", "ECDHE-ECDSA-AES128-SHA", "ECDHE-ECDSA-AES256-SHA", "ECDHE-RSA-RC4-SHA", "ECDHE-RSA-DES-CBC3-SHA", "ECDHE-RSA-AES128-SHA", "ECDHE-RSA-AES256-SHA", "ECDHE-RSA-AES128-GCM-SHA256"]
#This enables encrypted connections via HTTPS/2 over TLS
EnableHTTP2 = trueLast modified: February 16, 2024

