Identity Provider Connections
On this page
An Identity Provider Connection represents a connection between SingleStore Helios’s identity system and your IdP.
An organization may have zero or more IdP Connections.
Connections can be active or inactive, and they can be modified, copied, and deleted.
Each connection has an identifier and its own URL paths that need to be configured with the customer’s Identity Provider to make the connection work.
The process of establishing a connection involves exchanging information between the SingleStore Helios’s identity system and your IdP.
Both OIDC 1.
Domains
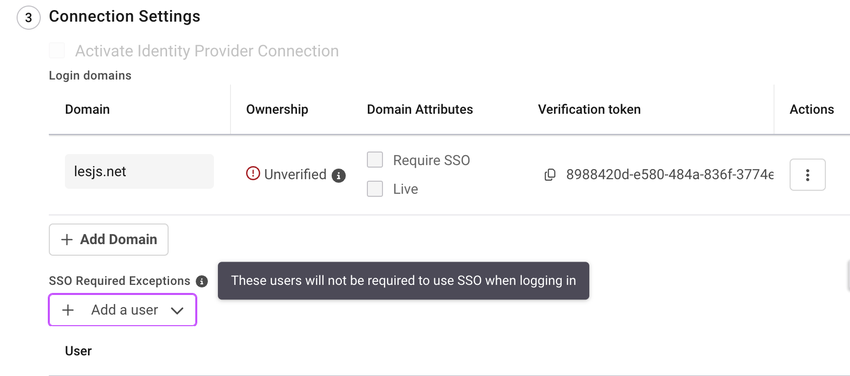
Each IDP connection is also configured with one or more domain names.
A domain can either be live or not live, on a per-IdP connection basis.
A domain can either be verified or not verified.
-
Create a DNS TXT record with the token as specified in the UI.
-
Create a web page with the token as specified in the UI.
Once a domain is verified, it remains verified.
To semi-automatically verify the sub-domains of a verified domain, select Verify.
An IdP connection cannot be activated without having at least one live and verified domain.
Multiple Organizations
If you have multiple SingleStore organizations that include users with the same email domain, set up SSO with only one of the organizations.
When setting up SSO, ensure that each email domain maps to a single SSO configuration.
Settings
One of the per-domain settings controls whether a non-SSO login is permitted when using an email address that matches the domain.
A list of email addresses of the form username or username@domain can bypass the per-domain Require SSO setting and log in through Keycloak.
Last modified: November 26, 2024

