Cloud Key Management Service for AWS Volume Encryption
On this page
Note
This feature is available in SingleStore Helios with Enterprise edition.
Overview
Amazon Elastic Block Store (EBS) encryption is supported by all EBS volume types and includes a built-in key management infrastructure.
There are two types of CMK: AWS-managed and customer-managed.
This guide provides instructions on how to create a customer-managed key used for EBS volume encryption, define which users/roles can perform encryption operations with this key, and how to use this key with your SingleStore Helios workspace.
Caution
When using a customer-managed key shared with SingleStore Helios, you are accepting the additional terms, conditions, and potential risks pertaining to data availability and loss.
Should the CMK permissions be revoked, or the key deleted, SingleStore Helios will no longer be able to encrypt/decrypt your data.
Configuring CMEK While Deploying a Workspace Group
-
To create a customer-managed key for use with EBS volume encryption, log into the AWS Management Console and navigate to Security, Identity, & Compliance > Key Management Service.
-
Select the same region as for the workspace group.
-
Go to the Customer Managed Keys section on the left side.
-
Click on the Create key button.
-
Select the Symmetric type.
-
Click Next till you reach the Key configuration page.
-
In the Cloud Portal New Deployment page, click on the Enable CMEK button below Advanced Settings and copy the suggested SingleStore policy.
-
Paste this into the Key policy section (don't remove the default code there, just add the policy with a comma).

-
Click on Finish.
-
After creating the KMS key you will see the ARN.
Copy this ARN and go back to the Cloud Portal ). 
-
In the Cloud Portal paste the ARN into the Data Bucket Key ID field.
The Backup Bucket Key ID (optional) field can be used for creating a backup bucket in AWS. You can paste either the same ARN or the ARN from another KMS key, but all keys should be in the same region as the workspace group. 
-
After creating the workspace group, go to the Security tab and if everything is configured correctly you should see the ENABLED status (If you provided both keys: dataBucketKeyID and backupBucketKeyID you will see two lines there).

Configuring CMEK During Replication
The replication process has the following dependencies for configuring CMEK:
-
if CMEK was not configured for the first workspace group, the CMEK button is not visible for configuring it for the secondary region;
-
if CMEK was configured for the primary region - you cannot add a DB to the replica without configuring CMEK for the secondary region as well.
This is mandatory. -
Only the owner and operator roles can set up CMEK when setting up replication.
-
CMEK can be configured only once and after saving you cannot change the settings after failover/failback or adding a new DB to the workspace group.
To configure CMEK in the secondary region, the steps are as follows:
-
Go to the Replication tab in the Cloud Portal and click on the Configure Replication button.
-
Ensure the secondary region is selected correctly and then click the Configure CMEK button.
-
You will see a new window with the CMEK settings.
A valid ARN should be pasted into the Data Bucket Key ID field. The Backup Bucket Key ID (optional) field is responsible only for creating the secondary backup bucket. It can be the same ARN or ARN from another KMS key, but from the same region. 
-
You will see two policies:
-
the first policy is for the second KMS key.
Copy this policy and paste it to the KMS key in AWS (policy section) intended for the secondary region. -
the second policy further down is for the KMS key (AWS) that was configured when creating the primary workspace group.
-
Do not delete the existing policy for the primary region, just add the additional part separated by a comma.
(Keep the Enable CMEK window open always during the entire configuration. ) -

-
Options for Creating the KMS Key for the Secondary Region in AWS
There are two options available for creating the KMS key: the single-region key and the multi-region key.
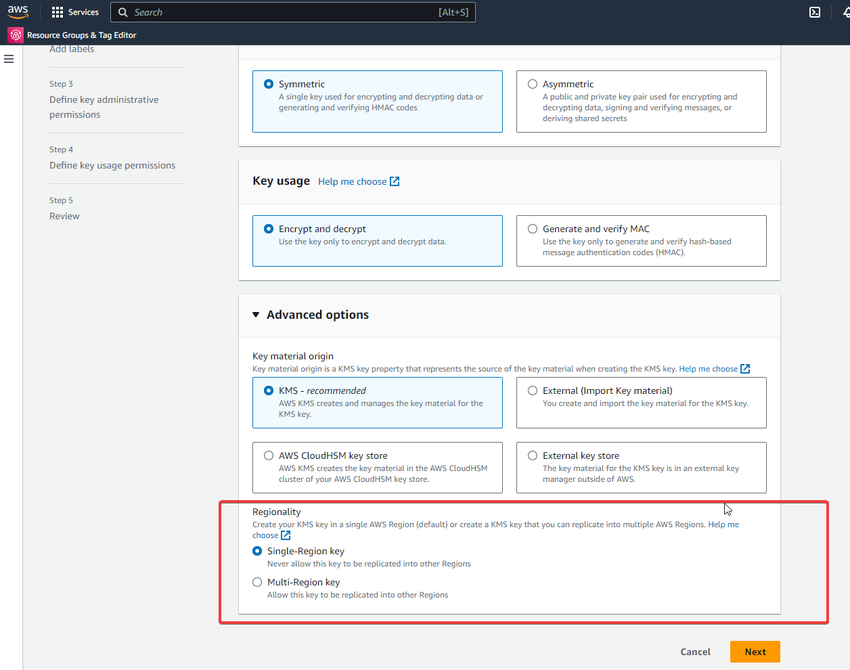
If you select the Single-region key, you can create only one KMS key in one region.
If you select the Multi-region key, you can create the first KMS key in the selected region and based on this key create new ones, in other regions (the policy and ID will be duplicated.
Select the replica region for the secondary region.
Go to the Cloud Portal, open the Replica tab, click on the Configure CMEK button.
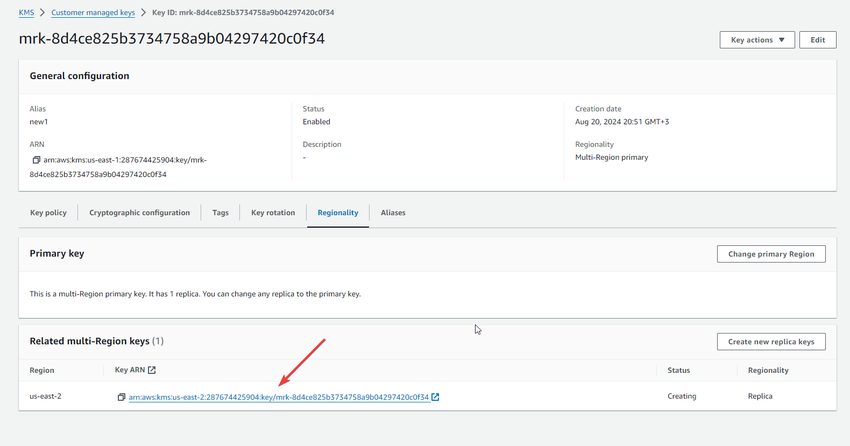
Open the just created KMS key and copy the ARN for pasting it to the Customer Portal to the Data Bucket Key ID field.
Update the policy for the primary region - copy the second part of the policy that SingleStore provides then go to the AWS region where the primary workspace group is located and open the KMS key that you used while configuring CMEK for the primary region.
Click on the SAVE button in the SingleStore and the replication process will start, the S3 bucket in the secondary region also will be encrypted.
Using API
If you use API while creating a new workspace group, you will not receive the SingleStore policy for the KMS key the first time.
If you use API while configuring replication, you will again not receive the SingleStore policy.
Last modified: May 22, 2025

